This simple post will take you through the process of adding an arbitrary file download exploit to mth3l3m3nt ; so yes no excuse to not have a working PoC for LFI or arbitrary file downloads because “I can’t code”. We will use the case of WordPress Plugin Membership Simplified v1.58 – Arbitrary File Download whose process of coming up with the payload has been discussed in the linked article.
The Payload is :
/wp-content/plugins/membership-simplified-for-oap-members-only/download.php?download_file=../../../wp-config.php
The first step is to go to the LFI exploits tab which looks something like below:
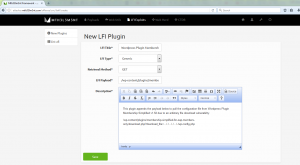
Click on the new plugin button ; to get a window on which we can create the attack.
A brief description of the fields seen to fill it right :
- LFI Title – This is a simple title ; i.e. whatever you wanna name your fancy new exploit e.g.
- LFI Type – Currently mth3l3m3nt supports two methods of injecting ; Generic (Uses the classic URL to inject) and cookie (injects payload into the cookie of the request)
- Retrieval Method – This is the header method to be used to retrieve e.g. send as a POST body or for classic versions use GET if the payload is meant to be in the URL for this case its going to be in the URL.
- LFI Payload – This is the actual attack string that is constant and will be appended in the request to determine the applicability of the exploit or not.
- Description- This is just some information that you might wanna put for reference as to the details of the exploit or discovery; further references etc.
Next we simply test it so click exploit on the plugin’s row. We will give it the target’s wordpress base page as the rest of the required URL is appended in the payload ; cross fingers.
You can now add exploit development to your CV 😉 you just made it.